If you ever used our ESP8266 Deauther, you might have wondered what the probe attack is for. We get questions like this a lot. So let's have a look at probe requests and what they are used for. 🕵️♀️
Active and Passive Scanning

If you open the WiFi settings menu on your phone, you'll see a list of available networks. But how does the phone know about them?
There are two ways to discover WiFi networks: either by passively waiting and listening for announcements (beacon frames) from access points or by actively asking every WiFi device around if they are a network using probe requests.
When an access point receives a probe request frame, it will reply with a probe response frame.
The Problem with Meta Data

Probe requests are a type of WiFi management frame. They are not encrypted, since they contain no user data. They are used simply for network discovery.
But it's common that a device will actively ask for a specific network name. Meaning the probe request will contain the SSID of a known network in cleartext. In other words, your phone might be leaking the name of your home network constantly. And not just that, it's probably broadcasting the names of every network you ever connected to!
This data can be used to identify you because your phone is likely to have a unique list of known networks. In addition, services like WiGLE can be used to pinpoint an SSID to a specific location.
So by simply listening for probe requests, you can track how many WiFi clients are nearby and where they have been. Plus the metadata provided by the MAC address of said clients like the name of the manufacturer (i.e. Apple).
Because WiFi clients tend to send probe requests regularly, it's possible to use mesh networks to track their movement. Systems like this could be used in locations like shopping malls to track the routes of customers.
Rogue APs

But it gets worse! Someone could collect the SSID from a received probe request, open a new WiFi network and give it the exact same name, then send a probe response. The client who sent the request will then automatically connect to that network, thinking it knows it. But really, it could be a malicious network that's sniffing all your traffic. Worst of all, the user might not even notice it because their device switched networks in the background without informing them.
This is actually a feature at what the WiFi pineapple from Hak5 excels at! So really this isn't some abstract theory, everyone with the right tools can pull this attack off.
Now that being said, there are limits to this attack. For example, if the rogue access point is using a different kind of encryption than the original network (i.e. network is open instead of using WPA2), it won't work. The WiFi client will also refuse to switch networks if it's already connected to one with a stronger signal. So it's not guaranteed to work with every WiFi client all the time, but it is a very effective attack.
Probe Attacks

To answer the question of what the probe attack in the ESP8266 Deauther is for; it broadcasts a lot of probe requests with random SSIDs. This can be used to confuse probe request sniffers, like the mentioned WiFi Pineapple. Learn more about it in the video Testing WiFi Pineapple with ESP8266 Deauther.
Another form of abusing probe frames for attacking is to flood a specific access point with requests. If the access point doesn't recognise the attack and tries to respond to each request, it will actively participate in the attack. This is because these packets take up a lot of air time and spamming them will basically clog the wifi channel and you will no longer be able to use the network effectively.
Probe Request Sniffing
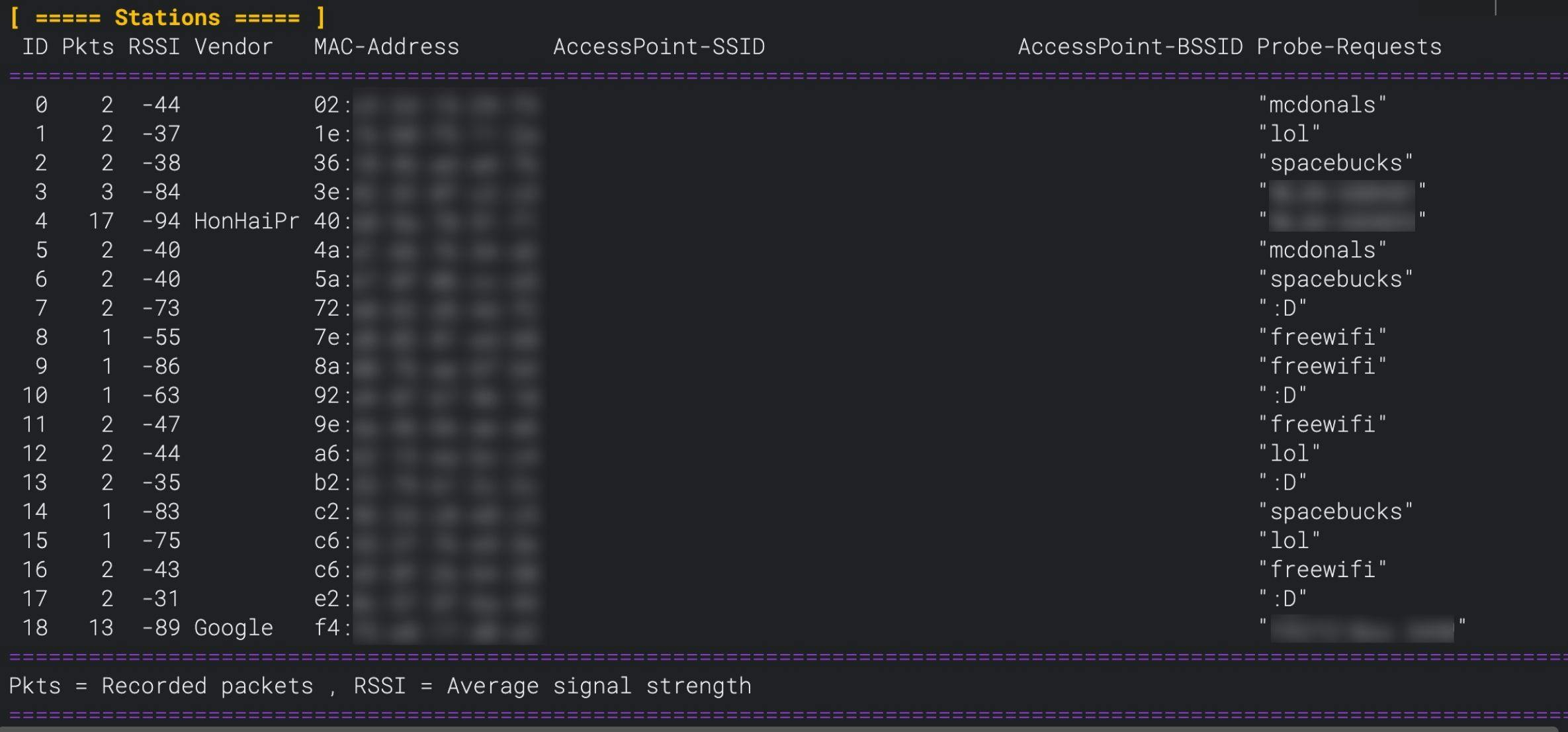
Now you know all about the dangers, but how can you check if your WiFi devices are sending probe requests?
Luckily for you, we make a tool that's capable of that. Our Deauther V3 can find WiFi devices and see the probe requests they're sending. You can flash any ESP8266 development board with the firmware or buy our Andromeda board at spacehuhn.store.
Alternatively, you can use airodump-ng (part of the aircrack-ng suite), Wireshark, or a script like probeSniffer. But you will need a USB WiFi adapter that is capable of monitor mode.
MAC Randomization

One thing to look out for when scanning for probe requests is MAC randomization. Nowadays a lot of WiFi clients use randomized MAC addresses for sending probe requests. This makes it a lot harder to fingerprint and track a device. You can easily get the impression that there are more devices around than there actually are.
If you want to learn more about MAC randomization and its limits, have a look at: Why MAC Address Randomization is not Enough: An Analysis of Wi-Fi Network Discovery Mechanisms

